Thread
Ethereum Users: Beware of Scams!
99% of users don't know what's happening behind the scenes and scammers are taking advantage.
This guide will help you avoid scams and recover if you are victimized.
A must-read for all Ethereum users, regardless of experience 🧵👇.
99% of users don't know what's happening behind the scenes and scammers are taking advantage.
This guide will help you avoid scams and recover if you are victimized.
A must-read for all Ethereum users, regardless of experience 🧵👇.
👛 Wallets
A wallet is something that holds the keys to your crypto, backed up with a seed phrase.
Your wallet doesn't actually store any crypto; the blockchain does.
It's your private keys that prove you're the owner of that wallet.
A wallet is something that holds the keys to your crypto, backed up with a seed phrase.
Your wallet doesn't actually store any crypto; the blockchain does.
It's your private keys that prove you're the owner of that wallet.
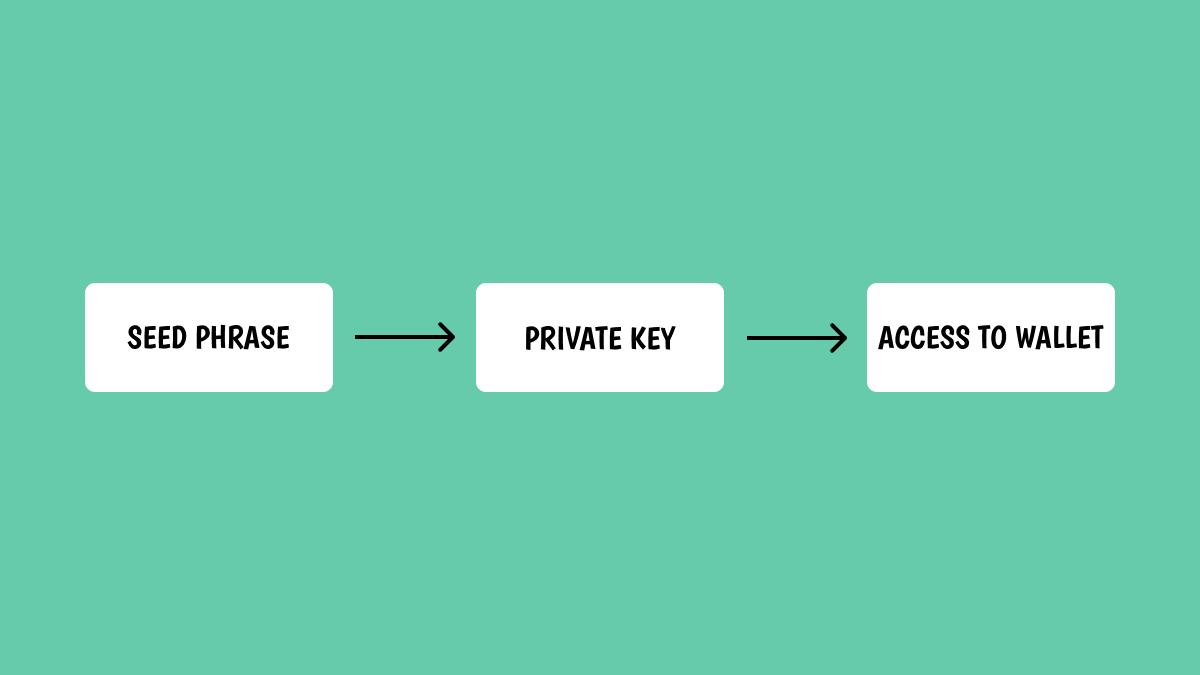
🛡️ Seed Phrase
A seed phrase is a set of words that is used to generate a sequence of private keys.
If your seed phrase is compromised, it can be used to gain access to your funds.
Therefore, it's crucial to keep your seed phrase safe and secure offline.
A seed phrase is a set of words that is used to generate a sequence of private keys.
If your seed phrase is compromised, it can be used to gain access to your funds.
Therefore, it's crucial to keep your seed phrase safe and secure offline.
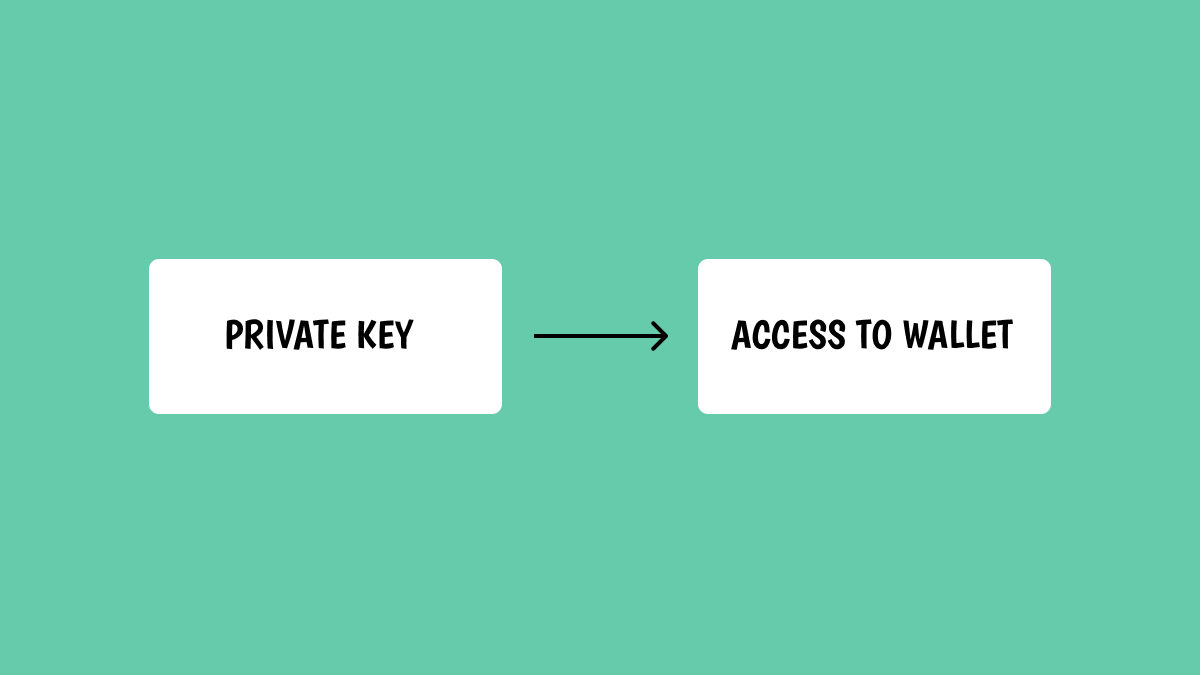
🔑 Private Key
A private key is a sequence of code that proves ownership of a cryptocurrency wallet and enables sending and receiving funds on the blockchain network.
If compromised the attacker will have full control over that specific address.
A private key is a sequence of code that proves ownership of a cryptocurrency wallet and enables sending and receiving funds on the blockchain network.
If compromised the attacker will have full control over that specific address.
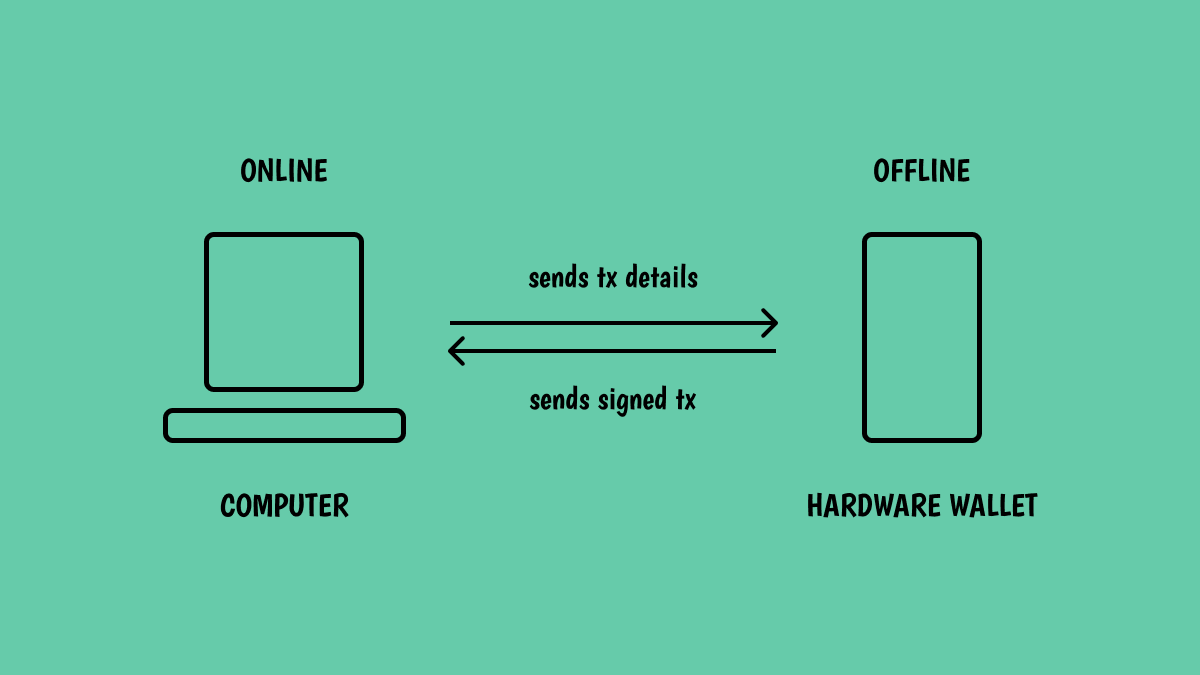
🔒 Hardware Wallet
A hardware wallet securely stores and isolates private keys from the internet to prevent compromise.
Transactions are initiated in a wallet and then you must physically sign them on the hardware device before it's submitted back to the network.
A hardware wallet securely stores and isolates private keys from the internet to prevent compromise.
Transactions are initiated in a wallet and then you must physically sign them on the hardware device before it's submitted back to the network.
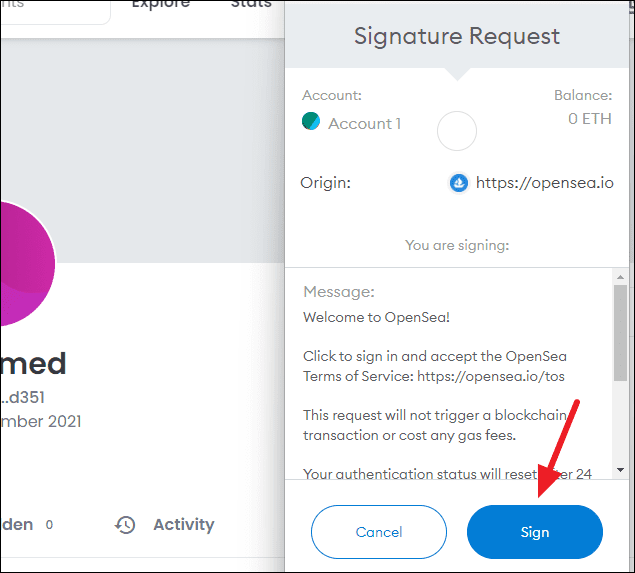
✍️ Signatures
Ethereum signatures verify transactions on the blockchain using a private key to sign and a public key to verify.
This ensures secure and authorized transactions.
Note: There are different signature types that have different implications.
Ethereum signatures verify transactions on the blockchain using a private key to sign and a public key to verify.
This ensures secure and authorized transactions.
Note: There are different signature types that have different implications.
👊 Attack Points
In the following section, we'll explore the top 3 ways that hackers try to gain access to your assets and how you can defend yourself against them.
In the following section, we'll explore the top 3 ways that hackers try to gain access to your assets and how you can defend yourself against them.
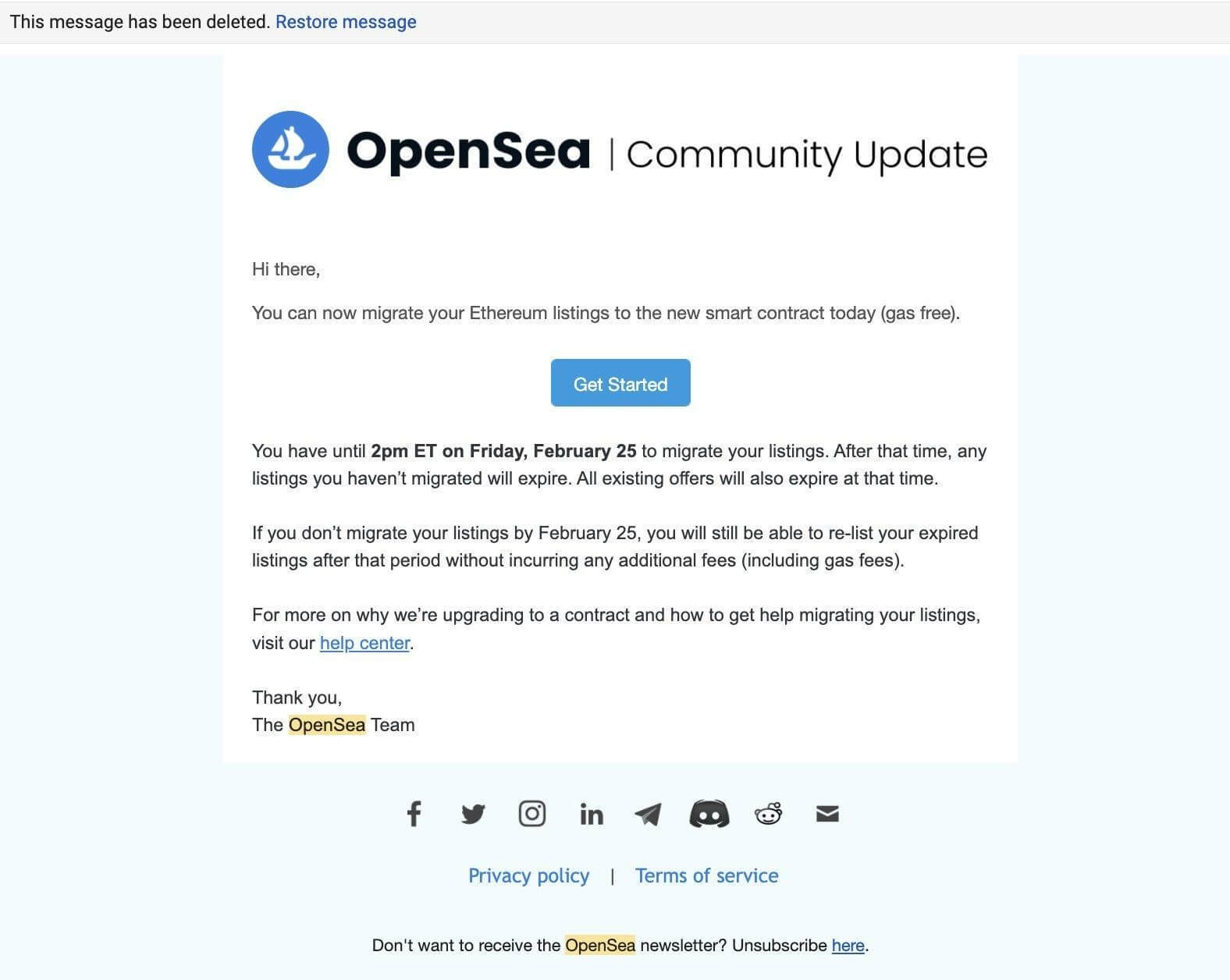
🐟 Phishing Attacks
Phishing attacks use fake websites or emails to trick users into revealing their private keys or sending funds to fraudulent addresses.
To protect against phishing, verify authenticity, and don't reveal private keys or send funds to unverified addresses.
Phishing attacks use fake websites or emails to trick users into revealing their private keys or sending funds to fraudulent addresses.
To protect against phishing, verify authenticity, and don't reveal private keys or send funds to unverified addresses.
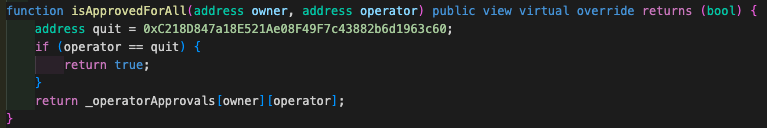
📝 Smart Contract Vulnerabilities
Smart contract vulnerabilities refer to code flaws in NFT contracts that hackers can exploit to steal or manipulate NFTs.
Protect yourself by reviewing the NFT contracts code (if you know how) or using reputable third-party security firms.
Smart contract vulnerabilities refer to code flaws in NFT contracts that hackers can exploit to steal or manipulate NFTs.
Protect yourself by reviewing the NFT contracts code (if you know how) or using reputable third-party security firms.
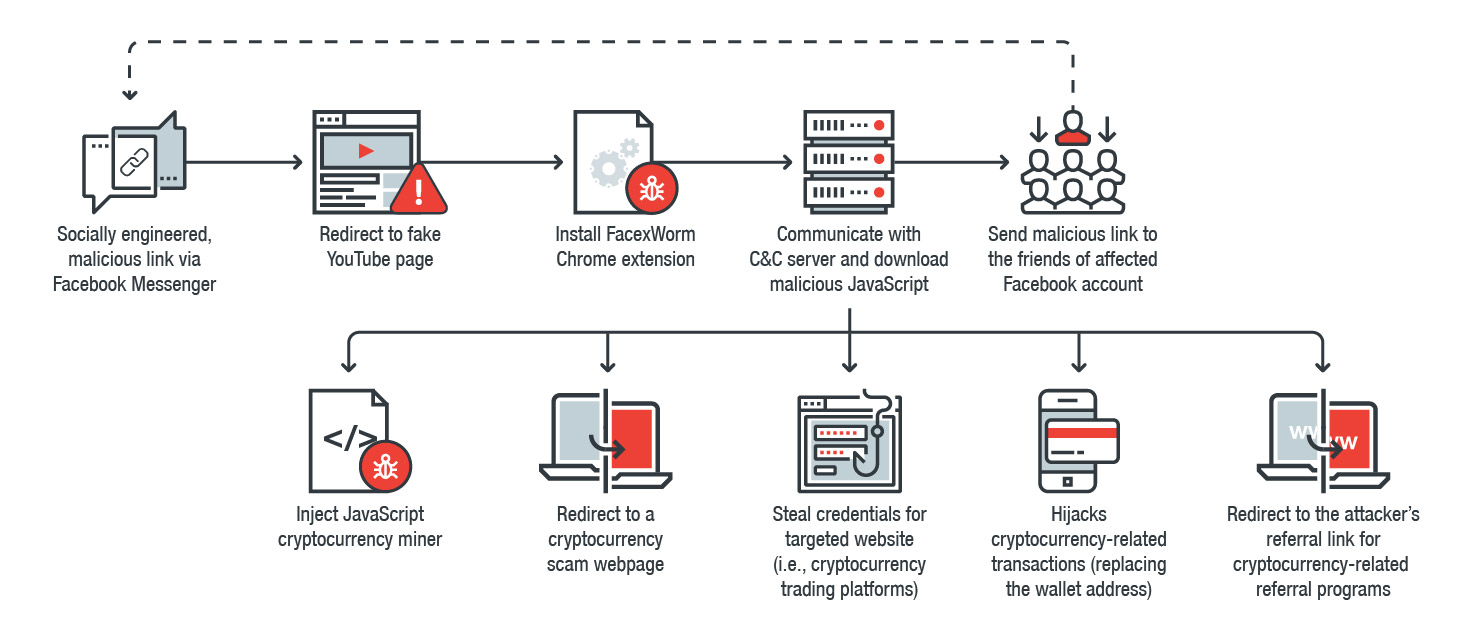
❗ Malicious Downloads
Hackers disguise malicious software as legitimate or use social engineering tactics to infect devices or steal sensitive information.
To help stay safe, only download from trusted sources and be cautious when dealing with suspicious emails or messages.
Hackers disguise malicious software as legitimate or use social engineering tactics to infect devices or steal sensitive information.
To help stay safe, only download from trusted sources and be cautious when dealing with suspicious emails or messages.
🔓 I've been hacked, what do I do?:
Recovering from a hack is dependent on the extent of the damage done.
To help you regain control:
• Assess the situation
• Identify how the hack took place
What's lost is lost, but taking these steps can minimize future damage.
Recovering from a hack is dependent on the extent of the damage done.
To help you regain control:
• Assess the situation
• Identify how the hack took place
What's lost is lost, but taking these steps can minimize future damage.
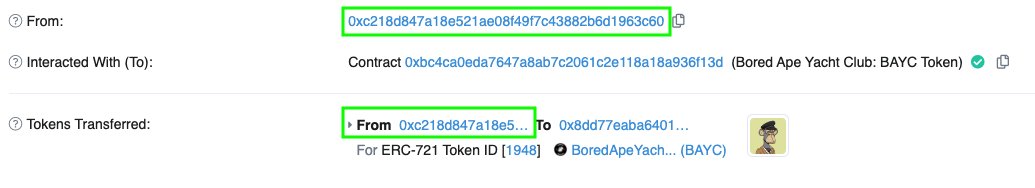
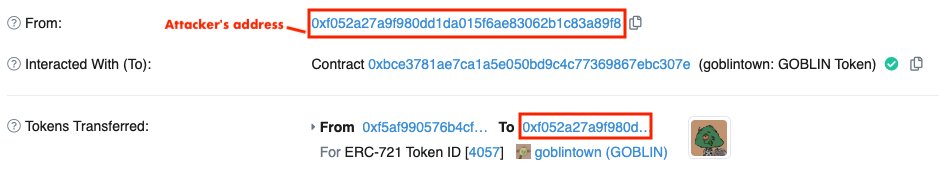
Lost NFTs?
Head over to Etherscan and check if your address initiated the transfer.
There are two possibilities - either you initiated it, or an attacker did.
Make sure you understand the implications of each one by referring to the images below.
Head over to Etherscan and check if your address initiated the transfer.
There are two possibilities - either you initiated it, or an attacker did.
Make sure you understand the implications of each one by referring to the images below.
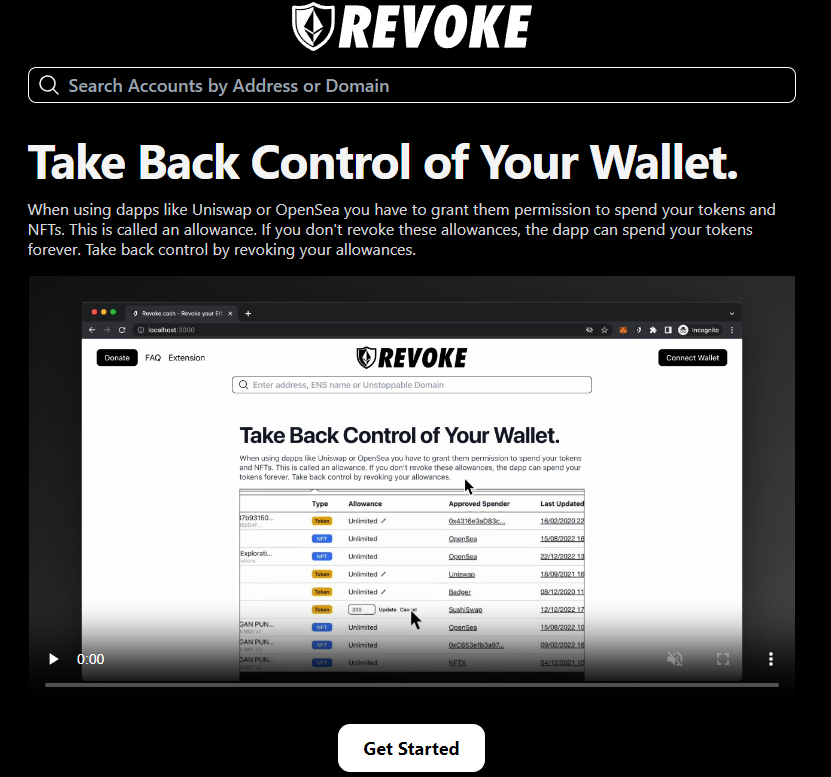
In case of an NFT being stolen via an attacker's address, there is a solution.
Head to @RevokeCash website to revoke any approvals.
It's the best way to take control back.
Head to @RevokeCash website to revoke any approvals.
It's the best way to take control back.
On the other hand, if the transfer is initiated by your address there are two possibilities.
1. You unknowingly fell for a scam
2. Someone has gained access to your private key
You can't recover what's lost but you can prevent further loss.
1. You unknowingly fell for a scam
2. Someone has gained access to your private key
You can't recover what's lost but you can prevent further loss.
Transfer everything that's left (if any) out of that address and never use it again.
If your private key is compromised, anything that gets sent to that address in the future will be immediately seized.
If your private key is compromised, anything that gets sent to that address in the future will be immediately seized.
Lost ETH?
Regardless of how the attack was carried out, once the ETH has been sent, it can't be retrieved.
ETH transactions don't require any approval for spending.
If you haven't authorized the sending of ETH, it's likely that your private key has been compromised.
Regardless of how the attack was carried out, once the ETH has been sent, it can't be retrieved.
ETH transactions don't require any approval for spending.
If you haven't authorized the sending of ETH, it's likely that your private key has been compromised.
To sum everything up:
• Don't download from untrusted sources
• Be overly cautious about anything you download
• Stick to reputable websites
• Get a hardware wallet
Take care and stay secure.
• Don't download from untrusted sources
• Be overly cautious about anything you download
• Stick to reputable websites
• Get a hardware wallet
Take care and stay secure.
You don't know the impact of losing an asset until it happens to you, let's spread awareness and help keep everyone safe by:
1. Sharing this so others can read it
2. Follow @Nook_NFT for more content like this
1. Sharing this so others can read it
2. Follow @Nook_NFT for more content like this